
Firewall, The First Layer of Passive Defense Strategy
As a natural continuation to our October’s Cybersecurity thematic series, this post’s goal is to highlight all types of firewalls in existence, for both network appliance and server security management, along with their additional individual tricks of the trade.
- Review our Series 1 → Security Hardening Essentials to Keep Your Site Safe
- Review our Series 2 → An in-depth Dive into the World of the Content Security Policy (CSP)
Bare Functionality
The firewall is one of the most commonly known pieces of software that guard our online presence. Its function is to filter out the traffic, so that no unauthorized devices are able to connect to the inner network, through the outer network, whilst still being able to control which devices are to be granted connection to, allowing the establishment of communication with applications and websites, thus still being able to utilize their online content.
For years major companies over the world have depended on a large combination of software products in order to better their services and provide more functions and features to their clients, regardless of the company field of work. However, as time passes many of these companies have gone out of business, have ended their production and/or support for the given products and this is where problems regularly start to arise.
Security developers are no fools, they know that they cannot provide a solution to each case individually, but instead have to take a wider approach to things and craft creations such as the Firewall. There are several different types of firewalls, some of which are:
- A packet-filtering firewall which examines all isolated packets and is not aware of the packet’s context;
- A stateful inspection firewall examines network traffic and determines if a packet is related to another;
- A proxy firewall inspects packets at the application layer of the Open Systems Interconnection (OSI) reference model;
- An NGFW implements a multilayered method to integrate enterprise firewall capabilities with an intrusion prevention system (IPS) and application control.
The Importance of Having a Firewall Configuration
Security on an open network is becoming more and more important with each day. Following the growth of the Internet, the benefits of owning your own dedicated server can be felt on a global scale now. For many, their personal data and web service accessibility have become essential parts of their daily life routine. Having the benefit of accessibility leads to a service that is publicly available, making it wide open to unwanted and seemingly random connections.
Often conducted with the use of bots and spoofed IP addresses, it’s common on the open Internet to experience foreign login attempts, port scans, in addition to other intrusive activity. There are basic security and firewall methods that can help in the prevention of these activities from turning into a much more alarming issue.
External Security Measures
A great example for such a 3rd party defense would be Cloudflare’s DDoS protection services, which after applied includes features like browser integrity checking, which involves validating the user agent of the browser, as well as the IP address of the connecting side. That way, it can distinguish an actual user trying to connect to the website and deny connection to any other non-authentical traffic generating type events.
Cloudflare also has a built-in web application firewall (WAF) which is extremely hard to bypass even to the more sophisticated of attackers. It filters traffic by allowing only browser type user agents to connect to your website, as any other type would be malicious. It also monitors ongoing connections and notifies the administrative contact of a website if it establishes that anything out of the ordinary starts occurring.
By default, it will close any ports which are not in use, and you can limit which IP addresses can connect to certain open ports as well, for example, ports 2082 and 2083 for cPanel, making it so that only the administrator’s IP can even access the page, and refusing connection for any other connection attempts, providing you a very secure solution for your administration page.
In the unlikely event that somehow an attacker does manage to pass the above walls of security, the Cloudflare rate-limiting function will only allow them a few user-chosen amounts of login attempts after being put down into an on-lock mode. Afterward, a confirmation will be requested on the administrator’s email before being able to try and log in again.
Standard Network Firewall vs Web Application Firewall (WAF)
The core difference between these two is their basic functionality and appliance. The standard firewall only provides your internal network with the most basic traffic filtering options. Web Application Firewall (WAF) protects all your internet properties from commonly seen vulnerabilities such as cross-website online scripting (XSS) and cross-website online forgery requests (CSRF).
It also stops Brute force login attempts, SQL Injections, DDoS/DoS attacks, and many other of the major cybersecurity types of attacks listed in the top Open Web Application Security Project (OWASP) vulnerability list.
Breadwinners
When it comes to making our choice onto which Web Application Firewall (WAF) we will actively deploy to our server, the list of options certainly won’t fit a single page. In the FastComet server environment, our main layers of defense consist of ModSecurity and BitNinja.
ModSecurity is a special security ruleset, which over time has amassed a large pool of additional features and is now a crowd favorite option. It comes pre-installed on most of the management panels, such as cPanel/WHM and Plesk. It does its job extremely well, providing quality defense for both the server modules, operating system and installed applications themselves.
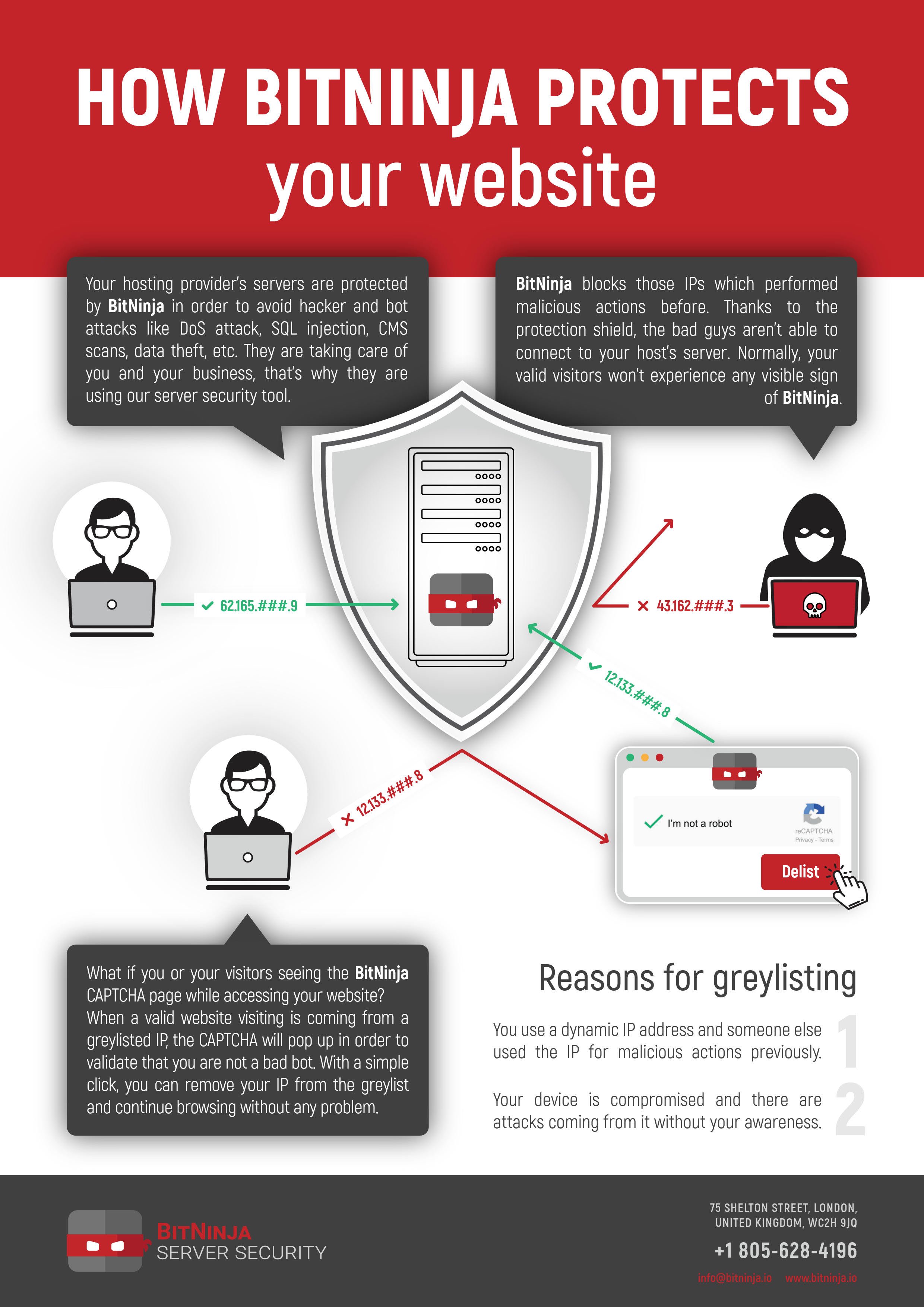
FastComet is also in a partnership with the 3rd party services provider BitNinja. The main focus of their product is to further strengthen the already present security setup of a server, adding the missing elements that may be found lacking. Once applied, the minimum ruleset you can set on your BitNinja settings prevents the following methods of exploitation.
- Web application vulnerability scanners
- Port scans
- Protocol attacks (loss of service)
- Remote code execution
- Code modification
- Remote File Inclusion
- PHP General Attacks
- Operating system version disclosure
- Blocks high-risk characters
While there will always be new ways to bend the rules and thousands of exploits are discovered on a monthly basis, a well established first line of defense will most certainly guarantee us a certain peace of mind that our content won’t fall into the hands of the general public.

The latest tips and news from the industry straight to your inbox!
Join 30,000+ subscribers for exclusive access to our monthly newsletter with insider cloud, hosting and WordPress tips!


Comments (1)
Our site has been down for over a day – DDos – so not sure this article is accurate.