
Why Using Legacy PHP Versions Makes Your Website Vulnerable
The most used scripting language is PHP. It’s rapidly evolving and after more than ten years without a significant upgrade to it, the scripting language introduced it’s 7.0 version. PHP 7 made a debut at the end of 2015. Recent years have witnessed the adoption of one very definite, while also consistent release process scheme. There has been a regular and predictable schedule new versions coming out every fall, earlier versions falling into maintenance, critical security issues, and the infamous End of Life (EOL) title. Each version gets supported actively for two years. Meanwhile, the third year gets only critical security-related updates. Using legacy PHP versions is bad for your site, and we will explain why.
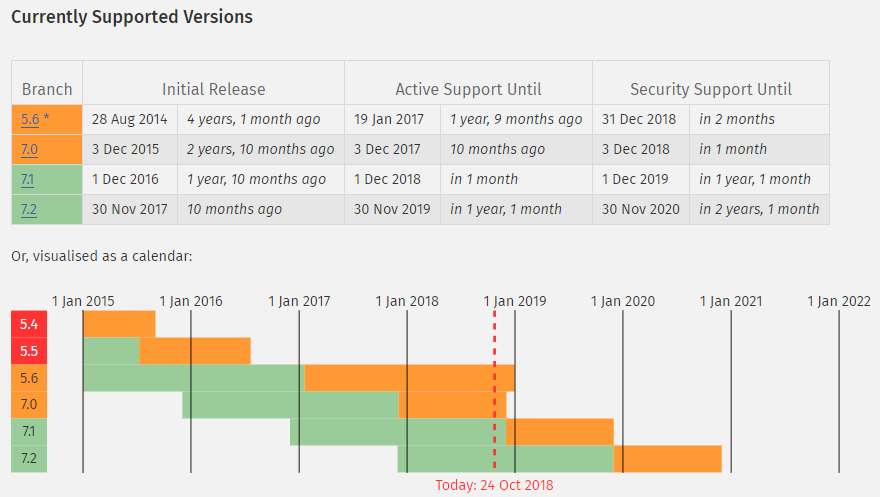
The last days of each year usually bring about a lot of reflection. A huge problem we are facing today is that many businesses, organizations, developers, and hosts have failed to keep up when it comes to supporting the latest versions of PHP. In fact, we’re 2 months away from a state where the oldest version which had been supported will be 7.1. Yeah, indeed.
Today we aim to discuss why it’s so vital for everyone to use those latest versions of the scripting language, and mainly from a security point of view. Below, you would also find some shocking statistics on why keeping PHP up-to-date matters to you.
The PHP Version Problem
Based on the W3Techs recent statistic report, roughly 79% of websites today are running on PHP. At the end of the year, scheduled by 31/12/2018, the security support for our dear chap PHP 5.6.x will be discontinued officially, marking the end of an era, which also means that all support for versions from the 5.x branch of PHP, which means that roughly 62% of all websites, running on a PHP version have reached their EOL.
Around 62% of all websites will run an unsupported PHP version in a few weeks
Therefore, starting off next year, around 62% of all websites that are still utilizing PHP 5.x would stop receiving their security updates due to the discontinuation of support. Inevitably, this will expose millions of websites around the globe to serious risks when it comes to security, which would also lead to poor performance. Consequently, if a hacker finds out about the vulnerability and decides to exploit it after New Year’s Eve, a lot of websites and users would be at risk.
WordPress and Its Current State
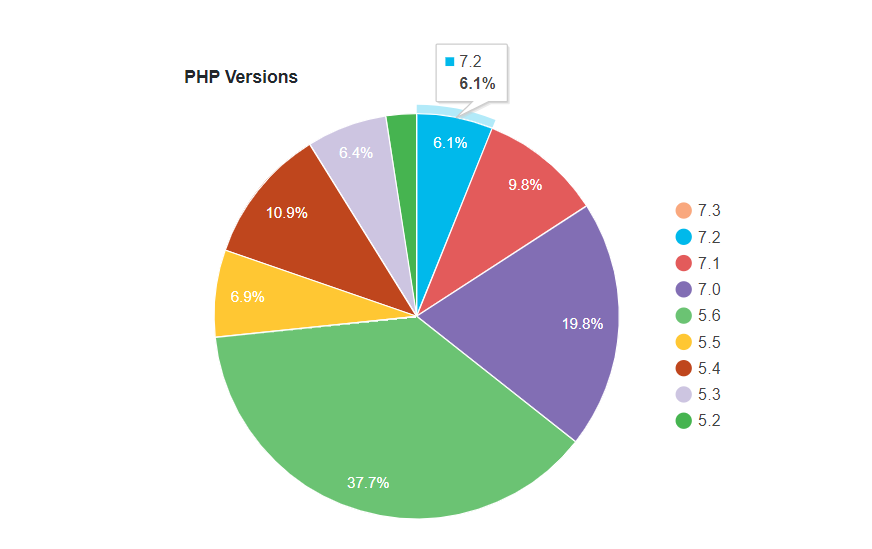
Based on official stats, around 36% of the WordPress users had already updated to PHP version 7 and higher and only 6% use PHP 7.2. Also, we can easily notice that a vast majority of the users over 37% continue to use PHP 5.6. What’s even scarier over 26% of all users run unsupported PHP versions. In December 2016, WordPress.org increased their official recommendation for users to go from the 5.6 to the 7 or higher version. As of summer 2017, WordPress has officially started recommending the use of PHP 7.2. The reason for that is because WordPress plans to continue being fully operational with some older versions of the scripting language the versions that have reached their EOL. An important thing to notice is the fact that WordPress, in its core in version 5.0, will support PHP 7.3.
At WordCamp Europe 2018, representatives from different teams got together to encourage people to increase adoption of the modern versions of PHP. This can be done by being more proactive and vocal when it comes to the necessity of the latest PHP versions. All of this aligns perfectly with the things that the community already advocates constantly update the core of your WordPress and its plugins. The same principle should also be applied to the PHP versions.
Is Running an Old Version Pure Madness or is It Just a Minor Security Risk?
You might be wondering: “Why can’t I just keep making use of the same version forever?” It’s a viable question, and we are able to shed some light on the matter.
Using any of the older versions comes with the risk of exposing you to certain security vulnerabilities, holes, bugs, etc. Those have been fixed in the more recent versions of the scripting language. If one goes to the National Vulnerability Database (NVD) XML feed, they will be able to find lots of security vulnerabilities of the previous PHP versions. The feed is provided on CVE Details and includes additional info of the updates’ impacts and severity. PHP 5 did, in fact, have a lot of vulnerabilities which were patched over time. If you’re interested, everyone can check the vulnerability library of the 5.4 version. Taking everything into consideration, if your website happens to be running on an older version of the language, some of the vulnerabilities may be still present and they can be easily exploited. Scary, huh? To make things even worse, the vulnerabilities are well known mainly among cybercriminals who constantly target websites that run on these earlier versions in order to easily exploit those projects.
Much of this bad reputation that WordPress gets for being insecure is often due to the servers and sites still running unpatched versions of PHP. In more than half of the cases, when a certain version becomes obsolete, the website owners are unable to update, install script updates quickly enough to ensure their site is secure, and in some cases, they are not even aware such update was needed. Which urges the question…
It’s Q4 2018, are you aware of what PHP version your site is using?

The latest tips and news from the industry straight to your inbox!
Join 30,000+ subscribers for exclusive access to our monthly newsletter with insider cloud, hosting and WordPress tips!


No Comments